CSTI-EDR – Endpoint Security Monitoring
-
Category:Industrial software & Digital TransformationInformation Security
- NO:03
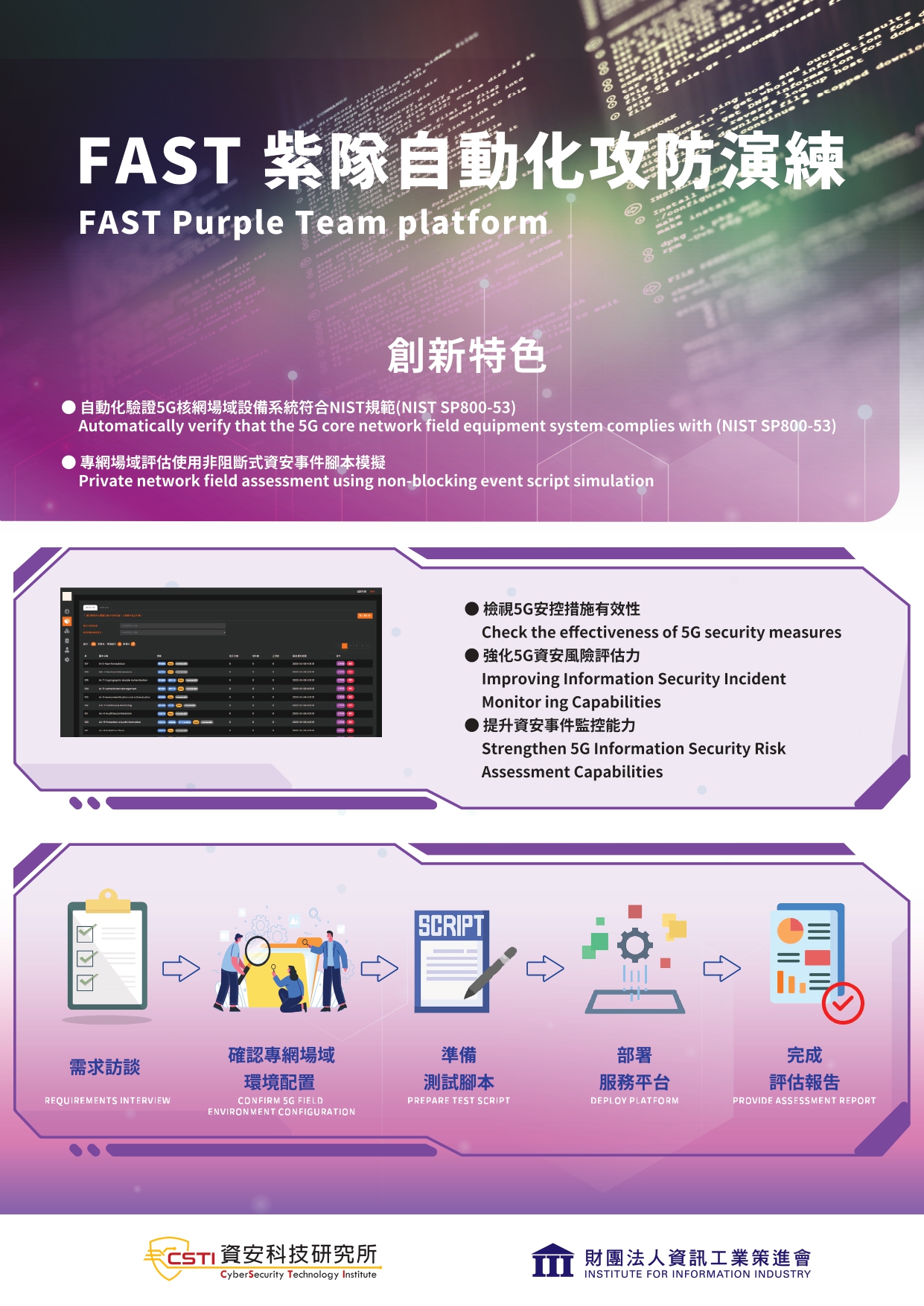
Integrate multiple OS logs and manage threat events in a single platform.
Unveil attack flow in real-time and correlate related endpoint logs to trace back cybersecurity incidents.
EDR – Endpoint Security Monitoring
●Support multiple operating system logs: Linux & Windows
●Identify APT attacks effectively with AI assistance
●TTPs based on MITRE ATT&CK framework
●Construct cybersecurity incidents with endpoint log analysis
Unveil attack flow in real-time and correlate related endpoint logs to trace back cybersecurity incidents.
EDR – Endpoint Security Monitoring
●Support multiple operating system logs: Linux & Windows
●Identify APT attacks effectively with AI assistance
●TTPs based on MITRE ATT&CK framework
●Construct cybersecurity incidents with endpoint log analysis

INSTITUTE FOR INFORMATION INDUSTRY CYBERSECURITY TECHNOLOGY INSITUTE
- Tel:912245399
Leading in serving the public sector in Taiwan, the Cybersecurity Technology Institute (CSTI) is aimed at providing technology solutions and services for its clients in confronting with emerging security challenges in cyberspace.
Introduction
CSTI was established in January 2012 by unifying III’s existing efforts in cyber security, including national policy formulation and deployment, technology R&D, solutions and services, etc. Having been successfully serving the public and private sector in Taiwan for more than 7 years, the CSTI teams will maintain their endeavor in national cyber security strategy planning, and developing technology solutions and services addressing vulnerability scanning, intrusion detection/protection, information sharing and analysis, security in cloud/internet of things/mobile networks, personal information management, etc.
Mission
‧ To plan and promote development policies related to digital nation, innovative economy, smart city and technology foresight application
‧ To play as a think tank in national ICT policy making, particularly cyber security
‧ To help strengthen the national cyber security capability with up-to-date technologies and solutions
‧ To develop innovative and advanced cyber security technologies and solutions
Business
‧ Formulating and deploying national ICT and cyber security policies
‧ Cyber security technology solutions and services in vulnerability scanning, intrusion detection/protection, malware analysis, security information sharing and analysis, security in cloud/internet of things/mobile networks
‧ Cyber security governance and personal information management solutions and services
‧ Software testing service for Web and mobile applications
Security Technology Research & Development Center
CSTI is aimed at developing new generation of core security modules and integrated security technologies, which include deep-learning vulnerabilities exploration, threat detection and defense, threat intelligence and malware analysis. At the core of the activities is the development of integrated solutions for cybersecurity. These include advanced penetration testing, web security, mobile application penetration testing, cloud security monitoring, enterprise dark net detection, user entity behavior analytics, threat intelligence and vulnerability management, etc.
In order to follow the government regulation about enterprise security governance and Personal Data Protection Law, techniques for security governance, risk monitoring and control, and security monitoring for threat identification have been developed to serve the public and private sector.
Introduction
CSTI was established in January 2012 by unifying III’s existing efforts in cyber security, including national policy formulation and deployment, technology R&D, solutions and services, etc. Having been successfully serving the public and private sector in Taiwan for more than 7 years, the CSTI teams will maintain their endeavor in national cyber security strategy planning, and developing technology solutions and services addressing vulnerability scanning, intrusion detection/protection, information sharing and analysis, security in cloud/internet of things/mobile networks, personal information management, etc.
Mission
‧ To plan and promote development policies related to digital nation, innovative economy, smart city and technology foresight application
‧ To play as a think tank in national ICT policy making, particularly cyber security
‧ To help strengthen the national cyber security capability with up-to-date technologies and solutions
‧ To develop innovative and advanced cyber security technologies and solutions
Business
‧ Formulating and deploying national ICT and cyber security policies
‧ Cyber security technology solutions and services in vulnerability scanning, intrusion detection/protection, malware analysis, security information sharing and analysis, security in cloud/internet of things/mobile networks
‧ Cyber security governance and personal information management solutions and services
‧ Software testing service for Web and mobile applications
Security Technology Research & Development Center
CSTI is aimed at developing new generation of core security modules and integrated security technologies, which include deep-learning vulnerabilities exploration, threat detection and defense, threat intelligence and malware analysis. At the core of the activities is the development of integrated solutions for cybersecurity. These include advanced penetration testing, web security, mobile application penetration testing, cloud security monitoring, enterprise dark net detection, user entity behavior analytics, threat intelligence and vulnerability management, etc.
In order to follow the government regulation about enterprise security governance and Personal Data Protection Law, techniques for security governance, risk monitoring and control, and security monitoring for threat identification have been developed to serve the public and private sector.